As noted earlier, there are software products for just about anything and everything imaginable. From games to programs designed to enhance professional development or monitor diet and nutrition, the list of possibilities seems almost limitless. Business software falls into the following categories:
Database management
Decision support
Word processing
Communications
Specialized use programs
Integrated software programs
DATABASE MANAGEMENT
Database management software allows for recording, modifying, and retrieving information without writing customized programs. Most database programs are designed to help users decide what type of information they want to record. They provide the means to enter, manipulate, and integrate the information to produce summaries, reports, or specific displays of items of interest. Most are set up to handle spur-of-the-moment inquiries, and allow records to be sorted and selected according to specific criteria. Examples of database software include PFS: File and Report and dbase III.
DECISION SUPPORT
The basic function of all decision support software, also known as financial modeling software, is to provide:
A quick and easy way to create mathematical models
Ways to enter information into the models
Reports of the results
These products can be broken down into three major categories: spreadsheets (VisiCa lc), financial modeling (IFPS), and integrated systems, which contain a database and graphing system (Lotus 1-2-3). All these products are designed to operate like an electronic multicolumnar accounting worksheet, except these worksheets have variable column widths with built-in math and financial models. Decision support software can be used to J)r1 pare budgets, analyze sales figures, calculate cash flow, or tiny other application where the information can be presented in a row or column.
WORD PROCESSING
Word processing packages allow for the creation, editing, and printing of documents, including correspondence and reports, form letters, legal papers, mailing labels, bills, and even book- length manuscripts. This book, for example, was written on a personal computer using one of the more popular word processing programs. The combination of word processing and personal computers offers more sophistication than can be found on a memory typewriter, and costs a fraction of the amount of a dedicated word processing system. The most fundamental component of any word processing package is its text editor. These editors are designed to edit a screenplay of text at a time, rather than line by line. They allow the user to scroll backward and forward through the text, rearrange it, copy it, delete words and phrases, add to an existing document, and, on some, check for spelling. Among the more popular programs are MultiMate, Word Star and the Volkswriter series.
COMMUNICATIONS
Personal computers that are linked together directly, or tied into host system, require the use of protocol software designed to allow two machines to talk with each other. A protocol is a standard that has been agreed to by hardware and software manufacturers so that different devices can transfer data between them. Without such a standard, two machines could not send or receive information at the same time or perform either function out of synchronization. A protocol provides a way for one machine to recognize that a line is tied up to the host, and that it must wait its turn. Protocols also provide the various sets of rules for controlling the transmission of information over any communications channel or cable.
Among the many functions protocol software programs perform are:
Establish and terminate the connection between two systems Maintain the integrity of the transmission through error detection procedures and requests for retransmissions Identify the sending and receiving machines handle a variety of special control functions, such as status checks, to make sure everything is working properly. Some software programs also provide a means to scramble and unscramble data communicated over telephone lines in order to protect the security of the information.
Among the more popular of these products are PC-Talk, Smart com II, and Crosstalk.
SPECIALIZED USE PROGRAMS
Specialized use packages fall into several groups:
Programs that support other software packages or enhance their use
Software that provides a specialized service, sometimes run- fling concurrently with another program
Graphics programs
Among the various packages available for specialized use are those that:
Run desktop organizers, which feature calculator, message board, telephone dialing, and appointment calendar functions that appear as windows similar to those shown in Figure 28, that overlay whatever software you may be working on. Print spreadsheet applications sideways so that they fit into reports more naturally. Increase the computer’s processing speed. Enhance keyboard operations by memorizing keystroke sequences and consolidating commands. With a program such as this, commands that normally take six or seven keystrokes can be reduced to one.
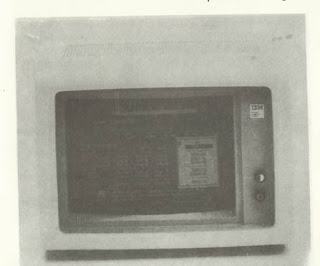
FIGURE 28. Monitor showing window display.
Produce presentation quality charts and graphs as shown in Figure 29.
Prepare line drawings, schematics, blueprints, and high resolution reproductions. The list of these specialized programs could go on. Most are available at a reasonable cost, usually for under $100, and many are offered free of charge through local personal computer user groups, or electronic bulletin boards.
INTEGRATED
SOFTWARE
Integrated software programs offer several major functions
in one package. Some of these offerings, for example, combine word processing,
database management, and spreadsheets along with some form of communications.
This is a one-stop-shopping approach, where you get everything in one place at
one price. These are large programs that require substantial memory
requirements on the order of 640K. Since they offer so much, they also have to
scrimp in places to get everything in. This generally means that they can’t
offer all the sophisticated features available in those programs that
specialize in just doing word processing or spreadsheets. Two examples of
integrated software are Symphony and Framework.
Before we finish :
If you need more help or have an opinion or suggestion Please leave a
comment Below. This is a Do-Follow Blog leaving a comment will also
help your blogs Google rank.